SABM =Set Asynchronous Balanced Mode
UA = Use Air Interface ?
SCCP = Signalling Connection Control Part
Explain:
a) Attach: What happens when the mobile attaches to GSM network?
When a mobile station is powered on, it performs a location update procedure by indicating its IMSI to the network. The first location update procedure is called the IMSI attach procedure. [1]
IMSI = International Mobile Subscriber Identity = MCC + MNC + MSIN
MCC = Maintenance Control Centre
MNC = Mobile Network Code
MSIN = Mobile Subscriber Identification Number
b) Location area update: What is the meaning for location update and how the location area is defined?
The mobile station also performs location updating, in order to indicate its current location, when it moves to a new Location Area or a different PLMN. This location updating message is sent to the new MSC/VLR, which gives the location information to the subscriber's HLR. If the mobile station is authorized in the new MSC/VLR, the subscriber's HLR cancells the registration of the mobile station with the old MSC/VLR.
Location Update is a procedure the MS uses to inform the network about its location. Location Update may be either normal or periodical. [3:15]
Most of the subscriber data in the HLR is stable, i.e it is changed by the operator, not by the network itself. However, when a mobile subscriber is active and moves in the network, the relevant part of this data is 'copied' to the VLR concerned and the VLR address is stored in the HLR. This data transfer/copying is called Location Registration. Location Registration is done when an MS performs a Location Update. [3:27]
A Location Area (LA), identified by its Location Area Identity (LAI) number, is a group of cells served by a single MSC/VLR. [1]
The location area can correspond to a BSC service area but can also consist of cells from several different BSC service areas located in the same MSC service area. [12:286]
PLMN = Public Land Mobile Network
MSC = Mobile Switching Centre
(A location updating is also performed periodically. If after the updating time period, the mobile station has not registered, it is then deregistered. [1])
c) What is the meaning of the periodic location area update?
A location updating is also performed periodically. If after the updating time period, the mobile station has not registered, it is then deregistered. [1]
For reliability reasons, GSM also has a periodic location updating procedure. If an HLR or MSC/VLR fails, to have each mobile register simultaneously to bring the database up to date would cause overloading. Therefore, the database is updated as location updating events occur. The enabling of periodic updating, and the time period between periodic updates, is controlled by the operator, and is a trade-off between signalling traffic and speed of recovery. If a mobile does not register after the updating time period, it is deregistered. [2]
A Location Update is always done when the MS realises the Location Area has changed. A Location Update can also be performed frequently after a defined time interval. Then it is called Periodic Location Update. [3:27]
(Merkitään HLR/VLR :ään että puhelin on pois päältä)
d) Cell selection: Depending on the state of the mobile phone (switched off, attached, call established), what is the entity who selects to which cell the mobile should go?
Switched off: Ei mikään, koska puhelin ei ole edes verkossa kiinni.
Attached: Mobile Station
Call established: Switching an ongoing call to a different channel or cell is called handover. Handovers can be initiated by either the BSC or the MSC (as a means of traffic load balancing). During its idle timeslots, the mobile scans the broadcast control channel of up to 16 neighboring cells, and forms a list of 6 best candidates for possible handover, based on the received signal strength. This information is passed to the BSC and MSC, at least once per second, and is used by the handover algorithm. [5:41]
BSC = Base Station Controller
MSC = Mobile Switching Centre
e) Paging: For what the paging is used?
Used to alert the mobile station of an incoming call. [2]
Paging is a procedure the network uses to find out a subscriber's location before actual call establishment. [3:15]
Paging is a separate procedure used in the case of a Mobile Terminated Call for Mobile Subscriber searching. Paging is initiated by the NSS and is based on the Location Registration information the Mobile Subscriber has supplied when performing the Location Update. [3:28]
NSS = Network Subsystem PAGCH = Paging Channel
(Location updating A powered-on mobile is informed of an incoming call by a paging message sent over the PAGCH channel of a cell. A compromise solution used in GSM is to group cells into location areas. Updating messages are required when moving between location areas, and mobile stations are paged in the cells of their current location area. [2])
Explain:
a) Authentication: How authentication is done in GSM, what network elements are involved with this process?
Authentication involves two functional entities, the SIM card in the mobile, and the Authentication Center (AuC). Each subscriber is given a secret key, one copy of which is stored in the SIM card and the other in the AuC. During authentication, the AuC generates a random number that it sends to the mobile. Both the mobile and the AuC then use the random number, in conjunction with the subscriber's secret key and a ciphering algorithm called A3, to generate a signed response (SRES) that is sent back to the AuC. If the number sent by the mobile is the same as the one calculated by the AuC, the subscriber is authenticated [2]
AuC lähettää Rand:n HLR:n kautta matkapuhelimen VLR:ään. MS laskee SRES:n Rand:n avulla. Auc laskee SRES:n ja lähettää myös sen VLR:ään. MS lähettää SRES:n VLR:ään. VLR:ssä vertaillaan SRES:it.[3]
AuC = Authentication Centre
SRES = Signed Response
(The authentication procedure involves the SIM card and the Authentication Center. A secret key, stored in the SIM card and the AuC, and a ciphering algorithm called A3 are used in order to verify the authenticity of the user. The mobile station and the AuC compute a SRES using the secret key, the algorithm A3 and a random number generated by the AuC. If the two computed SRES are the same, the subscriber is authenticated. The different services to which the subscriber has access are also checked. [1])
b) Key management: How the ciphering keys are generated?
A ciphering key is computed using the algorithm A8 stored on the SIM card, the subscriber key and a random number delivered by the network (this random number is the same as the one used for the authentication procedure). [1]
AuC laskee ciphering keyn salaisesta avaimesta ja Rand:sta, jonka jälkeen lähettää ciphering keyn VLR:ään, josta BTS sen saa salaamista ja purkamista varten. [3]
c) Ciphering location: Between which entities ciphering is used in GSM circuit switched communication?
Ciphering is used between Mobile Station and Base Tranceiver Station.
Ciphering procedure is used in the Air interface for speech and signalling encryption. When the authentication procedure has been completed succesfully for the Mobile Subscriber, the BTS and the MS may start ciphering procedure for further signalling and speech/data. [3:78]
clear <--> MS <- encrypted -> BTS <--> clear
BTS = Base Transceiver Station
MS = Mobile Station
d) Ciphering mechanism: How ciphering protocol works (draw a block diagram)?
The encryption algorithm A5 requires two basic values in order to start the ciphering. The basic values are KC and TDMA frame number. The TDMA frame is the format defining how the different signalling and traffic channels are located in the Air interface. Every frame is numbered in ascendic order from 0 to 2615647. [3:78]
Kaavio: [3:78]
clear <--> MS (A5, KC, TDMA) <- encrypted -> BTS (A5, KC, TDMA) <--> clear
e) Trust model: In the roaming case and during the authentication procedure, who trusts who?
Roaming: Uusi verkko luottaa siihen että vanhasta verkosta tulevat tiedot pitävät paikkansa ja MS luottaa molempiin verkkoihin.
Authentication: Molemmat luottavat toisiinsa (jaettu salaisuus). MS:n täytyy kuitenkin lisäksi luottaa AUC:hen vielä randomluvun osalta. Molemmat luottavat vielä VLR:ään että se suorittaa vertailun reilusti.
Explain:
a) Transparent vs. Non-transparent: What is the difference between transparent and non-transparent data?
Transparent Data Transmission: A method of transmission in which the transmission medium will not recognize control characters or initiate any control function. Transparent-based phones do not utilise any error correction. Thus the data sent and received MIGHT be corrupted unless a greater than two-bar cellphone signal is used (South African conditions). Non-transparent data uses a special ensure robust GSM-specific error correction technique called RLP for transmission. [6]
Non Transparent communication utilises a special GSM network-based error correction facility called "Radio Link Protocol" (RLP)that ensures more robust transmission. What this essentially means is that the GSM network's IWU will add special error correction codes to control the flow of data.
This ensures that the data transmitted first obtains a special acknowledgement signal from the receiver that informs the transmitter that the data has been received as transmitted and that the receiver is ready to receive the next set of data from the transmitter. If there is no such acknowledgement signal from the receiver, the networks will utilise their "data buffering" feature by using a special "forward correction" technique to ensure uninterrupted data transmission throughout. Not all cellphones support GSM's Non Transparent (RLP-based) data capabilities.
Transparent data transmission means that there is no GSM error correction supplied over the air interface.
Non-Transparent data only applies to data transfers and not faxing since the Group 3 standard for fax transmission is a transparent protocol. [13]
b) Delay requirements: How delay requirements of speech call information and data call information are different?
We find it difficult to accept delays in a telephone connection. Delay must be kept below a certain value so as not to be experienced as irritating, and variations can be inconvenient even if the total delay is moderate.
Data traffic, in contrast, is relatively insensitive to delay (within reasonable limits), whereas poor transmission quality can cause bit errors and a garbled message. [12:2:35]
c) Getting out of MSC: When speech call and data call gets out from the switch (MSC), what is the difference in routing the call?
Speech call:
The GSM transmission path for speech can be divided into the following
segments:
a) the mobile station
b) from the mobile station to the base station; the radio path
c) from the base station to the (remote) voice transcoder
d) from the voice transcoder to the MSC
e) from the MSC to receiver [kirja: 129]
Data call:
a) the mobile station
b) from the mobile station to the base station; the radio path
c) from the base station to the MSC
d) from the MSC to IWU (Inter Working Unit, special modem-like device)
e) from the IWU to AM (Analogue Modem)
The GSM-only components of these data/fax interfaces are not actually modems as we traditionally understand them: the "modem" component you need to send and receive data actually resides at the network headquarters (also known as the Mobile Switching Centre, or MSC), using a special modem-like device called an IWU, or Inter Working Unit.
Data is sent digitally from the PC via the special hardware adapter, through the phone and then through the air to the IWU. The GSM phone and the data/fax interfaces thus act as one extended digital "serial" or "air-interface" link between the PC and the IWU, which now acts as the Analogue Modem.
It is only when the digital data is received by the IWU that it is converted by the IWU to the analogue Frequency Shift Keys (FSK) tones characteristic of Analogue Modems, making it possible to connect via Telkom fixed-lines to an ordinary Analogue Modem. And if an ordinary fax machine or fax/modem sends data to your mobile phone, then the IWU converts the analogue tones received into the "digital data stream" suitable for transmission across the network to your GSM mobile.
If one mobile unit sends fax or data to another mobile, then there's no need for an analogue-to-digital conversion since the entire "air interface" is already digital, as is required by the GSM specification.[14]
d) Recovery of information loss: What happens if speech or data packet is lost in the radio interface?
In GSM, a slimmed-down version of link access procedure on the D-channel (LAPD) is used across the air interface. This link protocol is referred to as LAPDm. The protocol employs a mode of error detection based on the use of checksums. Errors are corrected in two different ways: either through retransmission or by simply discarding faulty signalling messages. [12:2:323]
e) Incoming calls: If a user has subscribed voice, data, and fax services and the mobile is attached to GSM network, how the user can control which kind of calls (voice/data/fax) she wants to now receive?
The problem remains when the only information received by the GMSC is the called number (the MSISDN). Two solutions of general application have been put on the table. The first solution consists of letting the service be chosen by the called party. The message setting the call from the network to the mobile station does not specify the service, and the mobile station indicates it in return. This solution imposes the requirement that the service is set by the user in the mobile station before the actual start of the communication. A typical scenario to send a fax to a GSM subscriber is then first to phone him (speech communication), asking him to set the mobile station so that the next call will be treated as a fax call; then hang up and re-dial to establish the fax call.
This solution has minimal impact on network, but is not very convenient for the users. This is why an alternative solution was proposed, consisting in providing a GSM subscriber with as many MSISDNs as services for which he wishes to receive incoming calls ( for instance a speech number and a fax number). The service can then be chosen by the calling party, by using the right number. The relationship between numbers and services is held in the HLR. [Kirja:524]
Soitettaessa datapuhelua gsm-puhelimeen, käytetään yleensä erillistä datanumeroa, Datanumeron avulla GSM-verkko erottaa tulevan datapuhelun tavallisesta puhelusta. GSM-verkon modeemi vastaa tulevaan puheluun ja GSM-verkko lähettää GSM-puhelimelle tiedon että sille olisi tulossa datapuhelu. Jos puhelu otetaan vastaan GSM-verkko yhdistää vastaanottavan modeemin ja kännykän ja soittavan modeemin ja kännykän välille on muodostunut datayhteys. [Petra]
If you want to receive data and/or fax via GSM, you must get and use the incoming numbers provided by your GSM network. You will thus have separate incoming numbers for Voice (your current cellphone number), Data at 9,600 baud, Data at 2,400 baud, and Fax at 9,600 baud.
Someone sending you data or fax will thus have to dial one of these incoming numbers to do so. To send you a fax via GSM, they must thus use your incoming fax number etc.
The reason for this additional numbering that not all the analogue fixed-line exchanges/switches can process and route the digital data that the digitally-based GSM networks and cellphones use. Thus the digital data must be fed through an appropriate incoming voice, data, or fax number. [13]
MSISDN = Mobile Subscriber International ISDN Number
Explain:
a) Mobile originating call: How mobile originating call is established from a mobile to fixed telephone network?
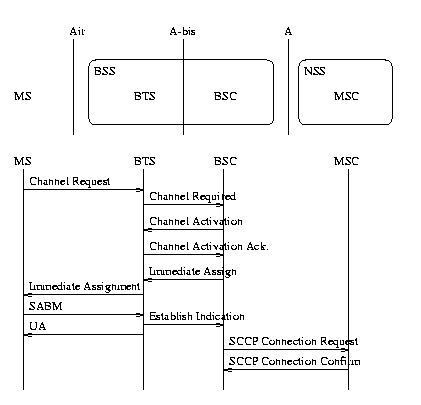
The BSS is located between two interfaces, Air and A. From the call establishment point of view, the MS must have a connection through these two interfaces before a call can be established. The MS starts the sequence by sending a message 'Channel Request'. This message contains a reason why the signalling connection through the BSS is needed. After this, the BSC allocates a signalling channel through so-called A-bis interface located between the BTS and the BSC. When the signalling channel is ready through the A-bis interface, the MS is told to move to the signalling channel in the Air interface. The MS informs it is on the signalling channel which then triggers the BSC to set up the A interface, i.e. the BSC requests the SCCP connection. When a signalling connection between the MS and the NSS has been opened as described, the MS starts the other signalling sequences in order to completed the original requested task. [3:24]

SABM =Set Asynchronous Balanced Mode
UA = Use Air Interface ?
SCCP = Signalling Connection Control Part
Where a traffic (speech, data) type of connection is concerned, the MSC initiates the procedure by sending an 'Assignment Request' message to the BSC. Within this message, the traffic channel through the A interface is taken into use. The BSC starts to allocate a traffic channel through the A-bis interface. As soon as the traffic channel is allocated through the A-bis, the BSC orders the MS to move to the traffic channel. The MS informs it is on the traffic channel to the BTS and, after this, the MS also informs the MSC about the same thing by sending as 'Assignment Complete' message.[3:24]
b) Mobile terminating call: How mobile terminating call is established from fixed telephone network to a roaming mobile?
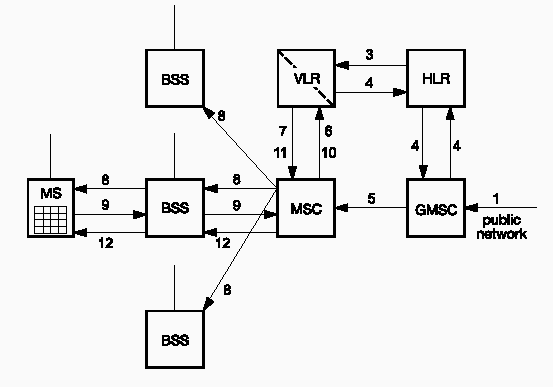
The incoming call is passed from the fixed network to the gateway MSC (GMSC) (1). Then, based on the IMSI numbers of the called party, its HLR is determined (2). The HLR checks for the existence of the called number. Then the relevant VLR is requested to provide a mobile station roaming number (MSRN) (3). This is transmitted back to the GMSC (4). Then the connection is switched through to the responsible MSC (5). Now the VLR is queried for the location range and reachability status of the mobile subscriber (6). If the MS is marked reachable, a radio call is enabled (7) and executed in all radio zones assigned to the VLR (8). When the mobile subscriber telephone responds to the page request from the current radio cell (9), all necessary security procedures are executed (10). If this is successful, the VLR indicates to the MSC (11) that the call can be completed (12). [5:36]
c) Data transfer: When a call has been already established, what is the difference in the speech data transmission in mobile originated and terminated calls?
Varmaankin väärin !!
In order to complete the mobile terminated call, the MSC must know the structure of the radio network located below itself.[3]
d) Location information: When subscriber A calls to subscriber B, how accurately A knows the location of B?
There are a number of technology alternatives for locating mobile phones, including network centric and handset centric solutions. The former build significant intelligence into the handset to achieve location whilst the later build more intelligence into the mobile network infrastructure.
Handset centric technology solutions include the Global Positioning System (GPS), overlay triangulation technologies based on timing or angle of signal transmission and reception at the handset (E-OTD, TOA) and Cell Of Origin (COO) information.
The only technology that is widely deployed in wireless networks today is cell of origin information. This scheme is used to meet Phase 1 911 emergency services requirements in the USA, wireless office location specific billing applications and some location-specific information request services.
Cell Of Origin (COO) requires no modification to the handset or networks and so is able to be used as the Location Finding System for existing subscribers but is less accurate than the other methods employed. Some would argue however that the accuracy of COO in cities is more than adequate for information services owing to the small cell size. The accuracy of COO is though questionable when the Location Finding System is required for assisting with emergency services.
COO is the only technology that is widely deployed in wireless networks today. This scheme is used to meet Phase 1 911 emergency services requirements in the USA, wireless office location specific billing applications and some location-specific information request services.
In this system, the mobile network base station (BTS) cell area is used as the location of the caller. Positioning accuracy generally depends upon the size of the cell but position down to 150 meters is possible in urban areas with the deployment of pico cell sites. Although other schemes offer higher degrees of positioning accuracy than cell of origin, its main advantages are that speed of response in getting a location fix is fast (typically around three seconds) and that as no handset or network upgrade is required, it can be used to provide location specific services to existing customer bases.
e) Billing: When two mobiles are roaming and subscriber A calls to subscriber B, who pays the bill?
There are TWO answers to this.
1) Automatic roaming. The caller is charged as if you're still in your home country. You pay the international leg of the call ie. from your country to the country you're in. If you have your phone set to divert on no answer, dirvert on busy etc to your voicemail, you pay for the leg back to your home country. So you pay for TWO international legs. If you set diversion you MUST set divert ALL calls and you will not be billed for any international legs.
b) Card Roaming. You are given a new number and callers calling you pay for the call to that country. You don't pay the international leg. the only inconvience is you don't have your old number, however a new voicemail message could inform callers of your new number. [7]
(Plastic Roaming is where you are given a new SIM card by your network that is to be used on a foreign network Automatic Roaming is when you just make the arrangements with your carrier before you go and turn you phone on when you arrive in the country you're roaming to. The bonus with Automatic Roaming is that you keep your number, the drawback is that you're charged heavily for calls.) [7]
Background information: Conventional GSM operates in a circuit mode, so that for each speech call a dedicated circuit is allocated. In the new GPRS packet service of GSM, the channel is allocated for the mobile only when there is something to send or receive (quite similar like in Ethrenet). Then, all GPRS mobiles are "sharing the same radio capacity"
Explain:
a) Operator's view: Compare circuit and packet switched services from operator's point of view
The fact that GPRS will operate at much higher speeds than current networks should provide a huge advantage from a software perspective. Today, wireless middleware is often required to allow slow speed mobile clients to work with fast networks for applications such as e-mail, databases, groupware or Internet access. With GPRS, wireless middleware will often be unnecessary, and thus it should be easier to deploy wireless solutions than ever before. [8]
Whereas today's wireless applications tend to be text oriented, the high throughput offered by GPRS will finally make multimedia content, including graphics, voice and video practical. Imagine participating in a video conference while waiting for your flight at the airport, something completely out of the question with today's data networks.
b) User's view: Compare circuit and packet switched services from the user's point of view
GPRS refers to a high-speed packet data technology, which is expected to be deployed in the next two years. It is expected to profoundly alter and improve the end-user experience of mobile data computing, by making it possible and cost-effective to remain constantly connected, as well as to send and receive data at much higher speeds than today. Its main innovations are that it is packet based, that it will increase data transmission speeds from the current 9.6 Kbps to over 100 Kbps, and that it will extend the Internet connection all the way to the mobile PC -- the user will no longer need to dial up a separate ISP. GPRS will complement rather than replace the current data services available through today's GSM digital cellular networks, such as circuit-switched data and Short Message Service. It will also provide the type of data capabilities planned for "third generation" cellular networks, but years ahead of them. [8]
The most important aspects of GPRS are that it allows data transmission speeds to over 100 Kbps, that it is packet based, and that it supports the world's leading Internet communications protocols, Internet Protocol (IP) and X. 25. [8]
The advantage of a packet-based approach is that GPRS only uses the medium, in this case the precious radio link, for the duration of time that data is being sent or received. This means that multiple users can share the same radio channel very efficiently. In contrast, with current circuit-switched connections, users have dedicated connections during their entire call, whether or not they are sending data. Many applications have idle periods during a session. With packet data, users will only pay for the amount of data they actually communicate, and not the idle time. In fact, with GPRS, users could be "virtually" connected for hours at a time and only incur modest connect charges. [8]
We now look more closely at how the user takes advantage of GPRS. We have already emphasized the packet nature of GPRS, which makes a GPRS connection similar in many ways to a local area network (LAN) connection. Just as with a LAN connection, once a GPRS mobile station registers with the network, it is ready to send and receive packets. A user with a laptop computer could be working on a document without even thinking about being connected, and then automatically receive new e-mail. The user could decide to continue working on their document, then half an hour later read the e-mail message and reply to it. All this time the user has had a network connection and not once had to dial in, as he or she must today with circuit-switched connections. Furthermore, GPRS allows for simultaneous voice and data communication, so the user can still receive incoming calls or make outgoing calls while in the midst of a data session.
Since there is almost no delay before sending data, GPRS is ideally suited for applications such as extended communications sessions, e-mail communications, database queries, dispatch, and stock updates to name just a few. In addition, the high throughput of GPRS will remove many of the obstacles from the use of multimedia, graphical web-based applications. For example, mobile users will be able to easily use graphically intensive web-based map application to get directions while traveling. Furthermore, with almost no transmission delay and high throughout, it will be more practical to use enterprise applications such as SAP* wirelessly and remotely. [8]
c) Applications: What kind of applications are good for circuit switched services, what are good for packet switched services?
Vastaus ylemmissä kohdissa.
Data services similar to those for GSM are also being developed for IS-136 TDMA and CDMA networks. But as a more mature digital technology, GSM has a strong head start. When GPRS is deployed, no other wireless data technology will be able to match its capabilities. But it is also important to remember that GSM already offers excellent data and fax capabilities that provide more than sufficient capability for many types of applications. As technologies like GPRS become available, the scope of data applications that are practical for wireless connectivity will only increase. [8]
Chat
Textual and Visual Information
Still Images
Moving Images
Web Browsing
Document Sharing/Collaborative Working
Audio
Job Dispatch
Corporate Email
Internet Email
Vehicle Positioning
Remote LAN Access
File Transfer
Home Automation, [9]
d) Network planning: Is there any difference for the operator, when using either circuit or packet switched services in respect of planning the network capacity (how many base stations are needed and where to place them)?
Packet switching means that GPRS radio resources are used only when users are actually sending or receiving data. Rather than dedicating a radio channel to a mobile data user for a fixed period of time, the available radio resource can be concurrently shared between several users. This efficient use of scarce radio resources means that large numbers of GPRS users can potentially share the same bandwidth and be served from a single cell. The actual number of users supported depends on the application being used and how much data is being transferred.
Because of the spectrum efficiency of GPRS there is less need to build in idle capacity that is only used in peak hours. GPRS therefore lets network operators maximise the use of their network resources in a dynamic and flexible way, along with user access to resources and revenues.
GPRS should improve the peak time capacity of a GSM network since it simultaneously:
* Allocates scarce radio resources more efficiently by supporting virtual connectivity
* Migrates traffic that was previously sent using Circuit Switched Data to GPRS instead, and
* Reduces SMS Centre and signalling channel loading by migrating some traffic that previously was sent using SMS to GPRS instead using the GPRS/SMS interconnect that is supported by the GPRS standards. [15]
Explain:
a) Roaming term: Explain in brief, what roaming means? Use a simple example.
The roaming feature allows a user to make and receive calls in any GSM network and to use the same user-specific services worldwide.
Example puuttuu.
b) Mobile's identity: How mobile (subscriber or terminal) is identified in the GSM network? How mobiles identity is related with roaming?
Mobile: IMEI (International Mobile Equipment Identity)
This number consists of type approval code, final assembly code and MS
serial number.IMEI numbes are stored in the network side in the
EIR. [3:79]
Subscriber: IMSI (International Mobile Subscriber Identity)
IMSI is a unique mobile subscriber identification number used both
within the GSM network nationally and partly internationally. The
network uses this number for identification and also security
purposes. The IMSI number is defined by the operator (partly) and it
is stored in the HLR, the AUC and SIM. [3:34]
Puhelin, jonka IMEI-numero on EIR:ssä mustalla listalla (tai harmaalla) ei saa käyttää palveluita.
c) Roaming agreement: When two operators are making a roaming agreement between themselves, what they agree, and what is then possible?
A roaming agreement is a business agreement between two network operators to transfer items such as call charges and subscription information back and forth, as their subscribers roam into each others areas. All GSM-enabled phones have a "smart card" inside called the Subscriber Identity Module (SIM). The SIM card is personalized to you and you alone. It identifies your account to the local network and provides authentication, which allows billing to the appropriate network. [4]
d) SS7 network: How SS7 network is used in the roaming? Is SS7 network needed if the mobile is not roaming but stays in the home network?
When a mobile station is switched on in a new location area, or it moves to a new location area or different operator's PLMN, it must register with the network to indicate its current location. In the normal case, a location update message is sent to the new MSC/VLR, which records the location area information, and then sends the location information to the subscriber's HLR. The information sent to the HLR is normally the SS7 address of the new VLR, although it may be a routing number. The reason a routing number is not normally assigned, even though it would reduce signalling, is that there is only a limited number of routing numbers available in the new MSC/VLR and they are allocated on demand for incoming calls. [2]
SS7:ää tarvitaan kotiverkossa kun siirrytään LA:sta toiseen.
e) Stolen mobiles: How it is quaranteed that stolen mobiles can't be used in the same country or taken into another country and used there?
Another level of security is performed on the mobile equipment itself, as opposed to the mobile subscriber. As mentioned earlier, each GSM terminal is identified by a unique International Mobile Equipment Identity (IMEI) number. A list of IMEIs in the network is stored in the Equipment Identity Register (EIR). The status returned in response to an IMEI query to the EIR is one of the following:
* White-listed
The terminal is allowed to connect to the network.
* Grey-listed
The terminal is under observation from the network for possible problems.
* Black-listed
The terminal has either been reported stolen, or is not type
approved (the correct type of terminal for a GSM network). The
terminal is not allowed to connect to the network. [2]
Background information: Conventional GSM operates in a circuit mode, so that for each speech call a dedicated circuit is allocated. In the new GPRS packet service of GSM, the channel is allocated for the mobile only when there is something to send or receive (quite similar like in Ethrenet). Then, all GPRS mobiles are "sharing the same radio capacity". It should be remembered also, that most limiting factor of operator's resources is the radio spectrum that may be very expensive (e.g., in USA, the spectrum costs a fortune).
Explain:
a) Billing of circuit switched services: What kind of principles operator can use for billing on the services used by GSM mobile users?
There are usually three main types of fees in the operators' charging
plans:
* Installation fee, which is a one-off cost
* Subscription fee, which is charged periodically; for example
quarterly
* Fees that are proportionate to the use of services. By service is
meant both basic network service (set-up of ordinary connections)
and possible supplementary services. [12:1:435]
b) Billing of packet switched services: What kind of principles operator can use for billing on the services used by GSM mobile users?
Laskutus voisi olla esimerkiksi tasainen kuukausimaksu tai hinnoittelu per lähetetyt paketit. Se, että laskutettaisiin erisuuria hintoja erilaisista paketeista olisi liian monimutkaista käyttäjälle kun taas kiinteät maksut suosisivat tehokäyttäjiä satunnaisia käyttäjiä enemmän.
Yksi melko optimaalinen hinnoittelumalli perustuisi kahteen muuttujaan - aikaan ja pakettiin. Verkko-operattorit voisivat määrätä nimellisen pakettihinnan suosituimpina aikoina ja kiinteän hinnan, ei pakettihintaa, muina aikoina. Näin kannustettaisiin epäsuosittuja aikoina kannustettaisiin käyttämään ja moneen tarkoitukseen tämä sopisikin, kuten esimerkiksi etämonitoroinnille, mittarinluvulle tai chattamiselle. Samaan aikaan, nimellin pakettihinta perittäisiin päivisin, jolla saataisiin allokoitua vähäiset radioresurssit niille jotka oikeasti niitä tarvivat ja raskaiden aplikaatioiden laskutus, kuten tiedoston ja kuvan siirto, olisi kovempaa kuin kevyiden. [Petra]
c) Roaming and billing: When a mobile subsriber is roaming, how the visited operator gets money for the services offered to a roaming mobile?
Ulkomailla soitetut puhelut laskutetaan aina ulkomaisen operaattorin verkon taksojen mukaan. Ulkomaiset operaattorit toimittavat Radiolinjaan puhelutiedot verkoissaan vierailevista Radiolinjan GSM-liittymistä. Näiden tietojen perusteella Radiolinja laskuttaa asiakkailtaan ulkomailla soitetuista puheluista. Kun Radiolinjan GSM 050 -liittymään vastataan muualla kuin Suomen alueella, vastaanottavalta liittymältä veloitetaan erillinen vastaanottomaksu. Ulkomailla vastaanotettu puhelu maksaa vastaanottajalle saman verran kuin puhelun soittaminen Suomesta ko. maahan Finnet-yhtiöiden taksan mukaan. Tämän lisäksi osa ulkomaanoperaattoreista veloittaa erillisen vastaanottomaksun. Näitä operaattoreita on esim. Yhdysvalloissa, Venäjällä ja Kaukoidässä.
Vastaanottomaksusta on sovittu kaikkien GSM-operaattorien kesken. Soittajahan ei voi etukäteen tietää, missä GSM-liittymään kulloinkin vastataan. Tällöin on kohtuullista, ettei soittavalta henkilöltä veloiteta ulkomaanpuhelun osuutta. [Petra]
d) Cost of the service: When a user is attached to Internet via either packet or circuit switched service and click a "web page of a nice picture", how the user can estimate how much it will cost to get the picture (of unknown size)?
Explain:
a) Subscription: When a mobile user subscribes a GSM voice call service from an operator, where the operator stores the subscription information?
All the subscriber information is stored permanently in the Home Location Register (HLR). [3:11]
b) HLR: What are the main functions of HLR?
HLR = Home Location Register
The HLR is considered as a very important database that stores information of the suscribers belonging to the covering area of a MSC. It also stores the current location of these subscribers and the services to which they have access. The location of the subscriber corresponds to the SS7 address of the Visitor Location Register (VLR) associated to the terminal. [1]
c) VLR: What are the main functions of VLR?
VLR = Visitor Location Register
The VLR contains information from a subscriber's HLR necessary in order to provide the subscribed services to visiting users. When a subscriber enters the covering area of a new MSC, the VLR associated to this MSC will request information about the new subscriber to its corresponding HLR. The VLR will then have enough information in order to assure the subscribed services without needing to ask the HLR each time a communication is established.
The VLR is always implemented together with a MSC; so the area under control of the MSC is also the area under control of the VLR. [1]
d) EIR: What is the usage of EIR
EIR = The Equipment Identity Register
The EIR is also used for security purposes. It is a register containing information about the mobile equipments. More particularly, it contains a list of all valid terminals. A terminal is identified by its International Mobile Equipment Identity (IMEI). The EIR allows then to forbid calls from stolen or unauthorized terminals (e.g, a terminal which does not respect the specifications concerning the output RF power). [1]
e) SMS: What are the main differences between short messages and IP datagrams?
SMS supports messages up to 160 characters in length. (?)
SMS is a bidirectional service for short alphanumeric (up to 160 bytes) messages. Messages are transported in a store-and-forward fashion. For point-to-point SMS, a message can be sent to another subscriber to the service, and an acknowledgement of receipt is provided to the sender. SMS can also be used in a cell-broadcast mode, for sending messages such as traffic updates or news updates. Messages can also be stored in the SIM card for later retrieval.
Lisäksi IP-paketeissa käytetään erilaisia headereita eri käyttötarkoituksiin ja SMS:ssä ei.
IP:ssä ei käytetä kuittauksia. Lisäksi IP-paketteja lähetettäessä vastaaonttajan täytyy olla aktiivinen pakettien saapuessa tai paketit eivät koskaan tule perille, kun taas SMS:t talletetaan jollei niiden vastaanottaja ole saapumishetkellä aktiivinen.
Explain:
a) Interfaces and reference points: In GSM there are both "interfaces" like A-interface and "reference points" like R/S-reference point. What is the difference between interface and reference point?
Interface: An interface presents the point of contact between two adjacent entities. [kirja:109]
Reference points: Points that demarcate the boundaries between functional groups. [12:2:501]
b) Abis-interface: In practical world, Abis interface is not really a multivendor-interface (same manufacturer sells to operator both BTS and BSC). What kind of impacts this has on BTS/BSC and Abis interface implementation?
c) Multivendor interface: Radio interface (Um) is a good example of multivendor interfaces. Explain, what are the benefits of such multivendor interfaces?
The main idea behind the GSM specification is to define several open interfaces which then are limiting certain parts of the GSM system. Because of this interface openness, the operator maintaining the network may obtain different parts of the network from different GSM network suppliers. Also, when an interface is open it defines strictly what is happening through the interface and this in turn strictly defines what kind of actions/procedures/functions must be implemented between the interfaces. [3:7]
GSM has been developed as a collection of open standards. This means that any manufacturer can develop any part of the system providing that the equipment presents the interface specified in the standards documentation. The result of this is greater participation in the development process leading to lower costs and more efficient equipment. [10]
d) Multivendor interface: Radio interface (Um) is a good example of multivendor interfaces. Explain, what are the disadvantages of such multivendor interfaces?
Niitä on vaikea määrittää niin että kaikki olisivat niihin tyytyväisiä, jolloin määrittely kestää kauan, mikä ei ole hyvä asia.
e) Type approval: Before a GSM mobile is allowed to be sold to public, the mobile must be "type approved". What is the reason for type approval of all mobiles (and base stations)? What are the disadvantages for type approval?
The cornerstone of GSM is international roaming. For this to be possible all networks and handsets have to be identical. With so many manufacturers creating so many products in so many countries, it was critical that each type of terminal was subject to a rigorous approval regime. Rogue terminals could cause untold damage to the new networks.
The crisis facing GSM operators in 1991 was that the type approval process simply wasn't available. In retrospect, it's easy to understand the reason for the delay. Such testing required the creation of a complex piece of equipment that simulated the entire GSM system in which the terminal would have to operate. The development of the simulator software turned out to be considerably more complex than had been envisaged. But without a testing process there could be no terminals and without the terminals none of the operators would be able to sign up customers. The situation was close to critical.
The solution was the introduction of interim type approval (ITA). Essentially, this was a procedure in which only a subset of the approval parameters was tested to ensure that the terminal in question would not create any problems for the networks. In spite of considerable concern expressed by some operators, ITA terminals became widely available in the course of 1992. True handheld terminals hit the market at the end of that year and the GSM bandwagon had finally started to roll. [11]
Full MS-roaming can only be achieved in the real world if common regulations are used by all countries in the domains of type approval, marking, free circulation and use of mobile stations.
Essential requirements to be met for type approval:
- User safety
- Safety of employees of public telecommunications network operators
- Electromagnetic compatibility requirements in so far as they are
specific to terminal equipment
- Protection of the public telephone network from harm
- Effective use of the radio frequency spectrum, where appropriate
- Interworking of terminal equipment with public telecommunications
network equipment for the purpose of establishing, modifying, charging
for, holding and clearing real or virtual connections
- Interworking of terminal equipment via the public telecommunications
network, in justified cases [kirja:585-586]
Explain:
a) Mobile terminating call: What happens to a mobile terminating call, if the mobile is not reachable?
1. The subscriber in the fixed network dials the B-subscriber's mobile number. The PSTN identifies the number and sets up a connection to the called network (GMSC).
2. The GMSC does not know through which MSC (or in which interworking mobile network) the mobile can be reached; nor does it know whether the mobile is free, busy, turned on or turned off. To be able to continue, the GMSC must therefore request a routing number from the HLR.
3. The registration function continuously updates the HLR on the location of the mobile (that is, in which MSC service area it is to be found) and the information showing if the mobile is turned on or off. Now, if the mobile phone is not reachable (turned off) the GMSC gets that information from the HLR and informs the subscriber. [12:2:351] (Osin myös omia ideoita)
If the subscriber has an answering service or something, the call can be directed to some other number. (HLR)
b) Mobile originating call: What happens to a mobile orginating call, if that mobile is out of coverage?
If the mobile is out of coverage (i.e not connected to the GSM network), it can't establish any calls. And ongoing calls will be terminated when the mobile phone gets out of coverage.
c) Out of coverage vs. out of power: How the network knows whether the mobile is out of coverage or out of power?
When mobile is switched off the network knows it, but if the mobile phone is out of coverage the network does not know that the phone is not active. If the mobile is out of coverage and someone makes mobile terminated call to that phone, the network pages the mobile phone several times and after not getting connection to that phone realises that the phone is not active.
The procedure of mobile report when it is turned off is called detachment in GSM. Information showing that the mobile is turned off is stored in the MSC that receives the information and in the HLR. Thus, if a mobile that is currently off is called from another network, the call will stop at the GMSC level. [12:2:351]
d) Power saving: To save mobile's power, it may sleep short while every now and then (e.g., by switching off the receiver for two seconds and then waking up for a short while, and going back to sleep). What are the impacts of this on mobile originating and terminating calls?
Mobile originated calls:
Minimizing co-channel interference is a goal in any cellular system,
since it allows better service for a given cell size, or the
use of smaller cells, thus increasing the overall capacity of the
system. Discontinuous transmission (DTX) is a method that
takes advantage of the fact that a person speaks less that 40 percent
of the time in normal conversation, by turning the
transmitter off during silence periods. An added benefit of DTX is
that power is conserved at the mobile unit.
The most important component of DTX is, of course, Voice Activity Detection. It must distinguish between voice and noise inputs, a task that is not as trivial as it appears, considering background noise. If a voice signal is misinterpreted as noise, the transmitter is turned off and a very annoying effect called clipping is heard at the receiving end. If, on the other hand, noise is misinterpreted as a voice signal too often, the efficiency of DTX is dramatically decreased. Another factor to consider is that when the transmitter is turned off, there is total silence heard at the receiving end, due to the digital nature of GSM. To assure the receiver that the connection is not dead, comfort noise is created at the receiving end by trying to match the characteristics of the transmitting end's background noise. [2]
Mobile terminated calls:
Another method used to conserve power at the mobile station is
discontinuous reception. The paging channel, used by the base station
to signal an incoming call, is structured into sub-channels. Each
mobile station needs to listen only to its own sub-channel. In the
time between successive paging sub-channels, the mobile can go into
sleep mode, when almost no power is used. [5]
e) Powering off: Is there any difference from the networks point of view whether the mobile is switched off by pressing the off-button or by taking the battery out?
Yes. When mobile is switched off the network knows it, but if the battery is taked off network does not know that the phone is not active. If the battery is taked off and someone makes mobile terminated call to that phone, the network pages the mobile phone several times and after not getting connection to that phone realises that the phone is not active.
The procedure of mobile report when it is turned off is called detachment in GSM. Information showing that the mobile is turned off is stored in the MSC that receives the information and in the HLR. Thus, if a mobile that is currently off is called from another network, the call will stop at the GMSC level. [12:2:351]
[1] An overview of the GSM system
[2] Overview of the Global System for Mobile Communications
[3] pruju
[4] Roaming with PCS using GSM 1900
[5] gsm.pdf
[8] General Packet Radio Service (GPRS)
[10] GSM Security
[11] GSM - a brief introduction
[12] Understanding Telecommunications
[13] Data/Fax-Over-GSM Tutorial
[14] What hardware do you need?
[15] Key Network Features of GPRS